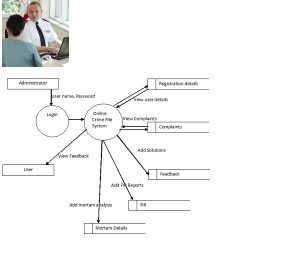
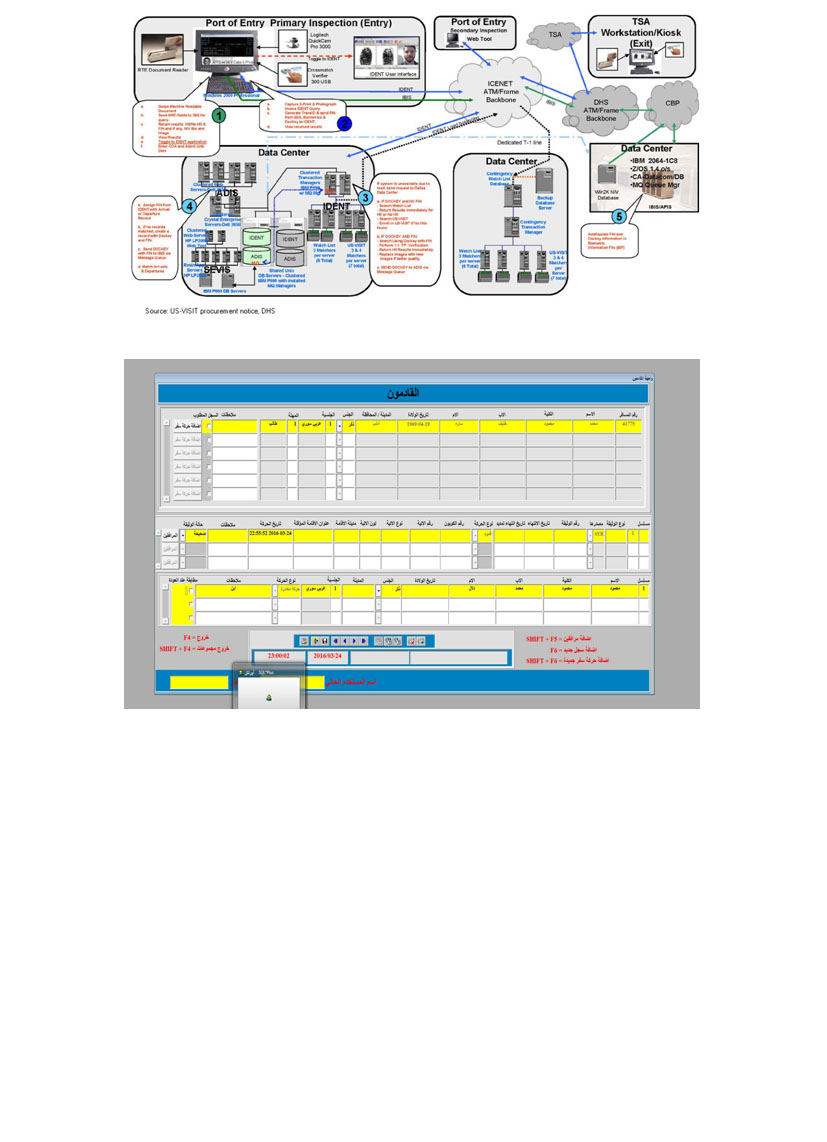
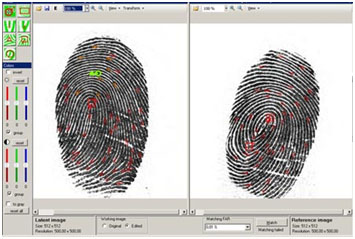
DNA fingerprinting works on the basis that each individual’s DNA structure – or genetic make-up – is unique and therefore cannot be forged, faked or altered in any way. Just like normal fingerprints taken from a suspect they are so unique that only in the case of identical twins – as we have already mentioned – could they be the same.
Statistically there is a one in sixty-four billion chance that any two unrelated individuals would have comparable DNA: comparable DNA is DNA that has certain attributes similar to that of another person but is not identical. This can be used as evidence in a court of law however most defence or prosecution counsels would tend not to rely heavily on it if there are only certain similarities.
One of the most common DNA fingerprinting procedures is RFLP: Restriction Fragment Length Polymorphism. Special enzymes are used to cut segments of a sample from which DNA is extracted. The procedure of RFLP focuses on repetitious sequences of DNA ‘bases’ which vary greatly from individual to individual.
These segments are then separated using a technique called Electrophoresis, which measures each of them by length. Once they have been sorted in this way a visual representation of the results is created using a procedure known as Autoradiography: basically producing an x-ray of the results that can be compared by overlapping the x-rays.
A more recent form of test is the STR Test (Short Tandem Repeat Test), which looks at DNA segments and counts the number of repeats at a number of different DNA sites – normally around thirteen.
Polymerase Chain Reaction – another more recent test – can create multiple copies of the DNA sequence using as little as fifty molecules; this procedure can help to produce a usable DNA sample from a single human hair.
It is worth noting that all of these tests have proven very reliable over the years and continual advances in forensic science – and genetic fingerprinting as a whole – have made these tests almost foolproof.